Table of contents:
What is Enterprise Data Protection?
Why Does Enterprise Data Security Matter?
Best Practices for Enterprise Data Protection
Enterprise Data Protection Solutions
Enterprise data protection is a crucial practice for any industry. It includes the upkeep, security, and defense of client and company information. The best way to guard against cyberattacks and data leaks is to have reliable enterprise data protection software. HQSoftware offers secure software systems that will save your sensitive data and help you establish clear protection policies. Relying on more than 20 years of experience in software development, we will examine what enterprise data protection services mean and what secure solutions you can employ to keep your information safe.
What is Enterprise Data Protection?
Why Does Enterprise Data Security Matter?
Best Practices for Enterprise Data Protection
Enterprise Data Protection Solutions
Enterprise data is any data that is produced, shared, handled, and stored by a company. This covers both organized information, such as shared documents and databases, and unstructured visual content, such as photos and video material. Enterprise data is typically stored in a data warehouse and is accessed by enterprise applications. It can be used to track customer behavior, understand financial transactions, and optimize business processes. Data privacy is the second most important core competency for professional security teams.
Enterprise data can come from a variety of sources, including internal systems like ERP or CRM software, external partners and vendors, and social media platforms. To effectively manage them, you can implement advanced data analytics tools and governance policies.
Enterprise data protection aids in avoiding data loss, fraud, identity theft, and cyberattack prevention. By safeguarding important data and enforcing security protocols, you can decrease the possibility of data breaches, protect their bottom lines, and ensure the safety of your customers. 92% of consumers think that preventive measures can stop data breaches.
The Symantec report on cybersecurity states that form-jacking attacks hit 4800 websites every month. According to сybersecurity statistics provided by the University of Maryland, a hacker attack occurs every 39 seconds on average. Thus, it is crucial to have appropriate enterprise-grade security measures, like encryption and secure storage, to protect the sensitive information you hold.
You can use the CIA triad (confidentiality, integrity, and availability) in developing a comprehensive approach to your data protection plan. The model includes:
Today, enterprise data security is essential for you to remain competitive and safeguard your reputation. The three primary enterprise data protection components are stringent access verification for the data you hold, adequate security policies to avoid cyberattacks, and reliable security solutions to keep the data secure. It is also important to inform your employees of the importance of data security by training them on how to safeguard the information they handle.
Enterprise data security matters because it ensures the confidentiality, integrity, and availability of personal and sensitive information. If mishandled, this data can be misused for identity theft, cybercrime, or other malicious purposes. Therefore, data protection measures such as encryption, access controls, and firewalls are necessary to prevent data breaches and maintain user privacy. Besides, failing to comply with data protection regulations can result in significant financial, legal, and reputational damage to a company.
Thus, data protection is not only an ethical responsibility but also a legal obligation mandated by regulatory bodies worldwide. For example, the Luxembourg DPA fined Amazon Europe the biggest penalties for GDPR infringement (746 million euros fine) as of 2022.
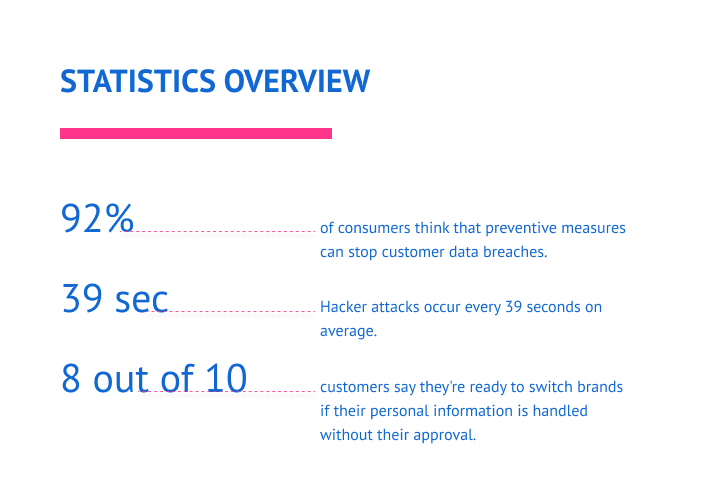
Additionally, you can benefit from data protection in terms of improved customer service (71 %), increased efficiency (68%), and improved brand reputation (69%). An estimated 8 out of 10 consumers say they’re ready to switch brands if their personal information is used without their approval. Information privacy can provide a competitive advantage, as it allows you to develop innovative services and goods that are difficult for rivals to imitate. It also helps to build trust with customers, as they feel more secure knowing their data is protected.
We frequently use enterprise data protection software such as firewalls, antivirus, and IAM for enterprise data protection. In addition to these technologies, you can also establish security guidelines and practices for appropriate data integration management.
At HQSoftware, we implement the best practices within our enterprise data protection services to ensure that our customers’ information is safe and secure. We have a dedicated team of experts who are responsible for monitoring our data protection practices and ensuring that they are up-to-date.

This includes a governance strategy that defines roles for each team member in the process of protecting enterprise data from potential threats. Proper monitoring and reporting should be implemented to deliver timely alerts on any breaches or other issues related to data security. Be certain that security precautions don’t hinder productivity or restrict employee access to information. Prevent criminals from obtaining personal information by taking preventative measures.
You must ensure your data protection strategies are effective and compliant with relevant regulations and laws. For example, the European Union’s General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CPRA, a later version of the CCPA), the Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada, or the Payment Card Industry Data Security Standard (PCI).
GDPR applies to every company that collects data or provides a service to EU residents. The law requires data breaches to be disclosed within 72 hours. The GDPR establishes stringent guidelines for the collection, processing, and storage of personal data. When gathering, storing, employing, and exchanging confidential data, enterprises must adhere to several rules. The GDPR applies to all sorts of personal user data. Personal data must be:
Compliance with these regulations is not only necessary to avoid hefty fines and legal action but also to maintain customer trust and safeguard sensitive information.
You should consider implementing intrusion detection tools to monitor your networks for indications of malicious activity or vulnerabilities that could be used by attackers. In order to safeguard the networks from external dangers and still permit authorized workers access when necessary, you must provide integration of security precaution systems, such as firewalls. You can make use of products like VPNs, which encrypt all data flowing through them and guarantee that only people with the proper authorization can access sensitive data stored on the network.
Training seminars should introduce the fundamentals of cybersecurity, including advice on avoiding potentially dangerous websites and attachments from dubious emails, and ensuring staff use accounts free of any personal information. They must additionally outline corrective measures that employees can take in case of security risks.
Security software refers to a variety of software that protects data, devices, and networks in various ways. Security software appears in many forms: antivirus software, firewall software, network security software, Internet security software, malware/spam removal and protection software, cryptographic software, ransomware, and more.
Want to create a data protection solution for your enterprise? We’re ready to help!HQSoftware has a team of skilled professionals ready to tackle the project. Let’s talk!
Anna Halias
Business Development Manager
With the increased use of cloud services, mobile devices, and the Internet of Things (IoT), you need to ensure that implementation of your enterprise data protection solutions is safe and secure from cyber threats. The best way to create reliable software is to hire a custom software development team.

At HQSoftware, we can offer:
The backup system is a complex client-server software that interacts with various file systems, hypervisors and databases for consistent backups. These solutions duplicate your data and store it in a secure place. If your data is deleted or damaged, you can restore it using the backup. Backups protect data from human error, hardware malfunctions, virus attacks, power outages, and natural catastrophes.
This software recovers information from a major data loss event, such as a natural disaster (disaster recovery solutions), a cyberattack, or even business disruptions. It is a program for regaining access and functionality to the company’s IT infrastructure. Recovery solutions allow you to restore the system files of your computer to its previous form. This allows you to undo modifications to your computer without affecting personal files such as email, documents, or visual material.
This software keeps your company operating both during and after a significant data loss. The idea behind business continuity is to have a program or a plan in case of emergencies or challenging circumstances. BCS is the company’s commitment to organizing efficient responses to operational and technical risks that could endanger its ability to recover.
IAM is a set of technologies and software products that meet the tasks of managing the life cycle of accounts and managing access to various systems in a company. IAM software systems manage user IDs and prevent access to corporate resources. The solutions verify that the appropriate people have access to the appropriate IT resources, at the appropriate times, for the appropriate purposes.
Among the most common types of malware that can infect digital data are viruses, worms, Trojans, spyware, and botnets. The risk of being detected increases when browsing malicious websites, opening infected email attachments, or using removable media. Phishing schemes, for example, frequently involve delivering infected links to bogus websites. These types of attacks often result in device failure or obtaining access to confidential data.
A firewall is a software-based system or hardware that mainly blocks and/or restricts incoming traffic from a computer or network. The main function of a firewall is to filter out malicious and dangerous infections. Each firewall can be set up to accept or reject a certain kind of traffic. Every message that passes through the firewall program is examined. Communications that don’t follow established security guidelines are forbidden.
IDS is a type of software that detects unauthorized and malicious activity on a computer network or on a separate host. The main objective of IDS is to detect the penetration of cybercriminals into the infrastructure and generate a security alert (there are no response functions, such as blocking unwanted activity in such systems), which will be transferred to the SIEM system for further processing.
DLP is specialized software that protects the organization from data leaks. It is a security tool that helps businesses ensure that private information, including IP addresses, Social Security numbers (SSNs), credit card details, trade secrets, financial data, and PII, does not leave the corporate network or get provided to a user without the individual’s consent. This technology is also useful for monitoring employees’ daily activities, allowing a company to identify security flaws before an incident happens.
Encryption is a method that uses mathematical models to transform confidential data into unreadable text. To restore this information to its original condition, an encryption key must be obtained. This information-protection technique has the versatility and capability to secure any type of information.
Tokenization is a data protection technique in which real information is replaced with tokens, data that serves no purpose and cannot be used for profit. Tokens chosen from a particular library serve as the basis for such a replacement, and they alter the actual data, increasing information security.
These solutions protect your enterprise data from criminals. Furthermore, consider regular security audits and risk analyses to find any potential security holes in their networks and systems. As well, we recommend using a preventative strategy for data protection.
Enterprise data protection services are vital for any business that deals with sensitive information. Your company may be subject to data breaches, which can have major financial repercussions for organizations, including penalties, legal fees, and customer compensation. You can run several risks if you don’t take data security threats seriously. Have a look at some of the main dangers of data loss below:
Failing to comply with security compliance regulations could lead to fines and legal disputes. Anyone may file a lawsuit against a firm and demand compensation if their data is compromised and stolen.
The company may suffer a competitive disadvantage if competitors have better data protection measures. In addition to the corporate and customer information that is at risk, enterprises run the risk of losing patents, trademarks, and other certifications.
Data leakage can damage the reputation of a company and turn off potential clients. Customers will lose faith in the business. This could damage the enterprise’s reputation and result in financial penalties.
The delay between a security event and restoration has a major negative impact on business operations, resulting in reduced productivity, a lost budget and development costs, and dissatisfied customers. Data protection is typically achieved through the use of security measures such as encryption, access control, and firewalls.
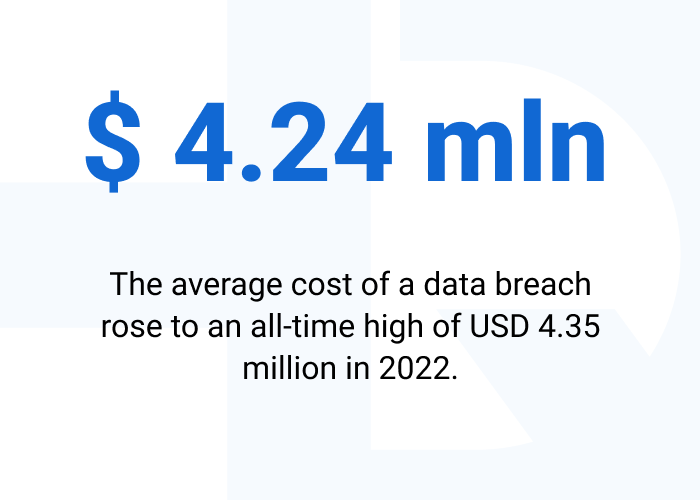
Losing of confidential data can lead to a loss of revenue and customers. The average cost of a data breach rose to an all-time high of USD 4.35 million in 2022. This represents a 2.6% rise over the average cost of a breach from the previous year, which was USD 4.24 million.
Be conscious of the need for robust data protection as technology and the digital environment continue to rapidly evolve. It’s about not only deterring cyberattacks, but also safeguarding customer and staff data. You must take appropriate steps to guarantee the security of your data, from verification to access control and data encryption. Choosing the right security software development company is important to keep your business safe. At HQSoftware, we engineer various types of enterprise data protection software in compliance with regulations, to defend your enterprise from cyber criminals and protect your company’s reputation.
If you have any questions about enterprise data protection services, please do not hesitate to contact us. We will be happy to answer any questions you may have.

Head of Production
To ensure the outstanding quality of HQSoftware’s solutions and services, I took the position of Head of Production and manager of the Quality Assurance department. Turn to me with any questions regarding our tech expertise.
We are open to seeing your business needs and determining the best solution. Complete this form, and receive a free personalized proposal from your dedicated manager.

Sergei Vardomatski
Founder